Mobile applications today function as more than mere tools because they represent business establishments’ primary entry points. Your mobile application is the initial and most common pathway through which your business interacts with customers. This engagement process applies to enterprise leaders as well as small business owners. But with opportunity comes responsibility. Users expect flawless performance alongside absolute security protection and continuous access that must work across every device type through all networks, even while on the move.
A 2025 Statista report shows that 90% of U.S. mobile users expect applications to operate with a speed below 3 seconds, and security-related concerns make 68% of users exit from apps. Mobile app security has become a business-critical priority because U.S. data breach costs reached $9.48 million on average.
This guide has been built to assist decision-makers, developers, and CTOs with the best mobile application security and performance standards. The guide examines every essential aspect, starting with encryption and authentication protocols, while addressing performance enhancement and offline functionality to guarantee that apps provide speed, security, and robustness.
Your application development needs will be supported through clear guidance that leads to confident construction and secure expansion.
Experience the Power of Mobile Application Development
Transformative Mobile Solutions for Your Business Growth
Explore Mobile App DevelopmentEncryption: Data in Transit & At Rest
Mobile-first operations require data to be continuously transferred between devices and servers through APIs and cloud services. The absence of strong encryption would endanger data from being intercepted for manipulation while allowing it to be stolen. The encryption process protects data from unauthorized use since intercepted information becomes indecipherable and useless to anyone who does not have permission.
Encrypt Everything, End-to-End
A secure connection using HTTPS/TLS needs to be established for every server data exchange. Each modern iOS and Android application must disable the use of bare HTTP. Since iOS, all apps are required to use secure HTTPS, and App Transport Security has implemented automatic blocking of insecure HTTP from the platform. Android users can access straightforward APIs such as HttpsURLConnection and SSLSocket for TLS encryption during transit, whereas you must always activate SSL protection for API communication. SSL pinning represents an optimal security measure for banking APIs since it embeds your server key or cert into the application to block “man-in-the-middle” attacks.
Secure Storage on Device
Encrypt user data at rest on the device. Both Apple and Google offer robust built-in encryption:
iOS
Leverage the Keychain and Data Protection APIs for sensitive information. The encryption provided by Keychain automatically protects all data storage along with Data Protection classes that maintain file encryption until user passcode authentication. Storing secrets in UserDefaults leads to security problems since this system lacks encryption protections.
Android
The Android Keystore system serves as the primary method for security purposes when handling keys and credentials. Full-device encryption exists in Android devices by default, although your application should build another security layer. Private keys, along with tokens, must be stored in the Keystore system rather than plain text prefs or files because the Keystore is a hardware-backed encryption system. The Jetpack Security libraries (including EncryptedSharedPreferences and EncryptedFile) help you save encrypted files and prefs that use strong security algorithms (such as AES-256) in a transparent manner. The protection of database data at rest should rely on encrypted database solutions such as SQLCipher or Room With Encryption. Google recommends that users store their keys in Keystore while choosing Tink, along with other tools for data encryption, with those keys.
Cross-Platform (Flutter)
Flutter enables app developers to apply native encryption methods that their applications can utilize. The flutter_secure_storage package enables the protection of sensitive data through iOS Keychain and Android Keystore storage methods. When using local databases with sqflite in Flutter applications, encrypt the databases when they contain personal or confidential information. The standard practice says that any information that should only appear on postcards for printing should never be stored as plaintext on mobile devices.
Authentication & Data Protection
User authentication must have secure processes that safeguard credentials alongside secure authentication protocols. It remains best practice to authorize user access through token-based methods like OAuth 2.0 while delegating identity authentication to trusted providers, as keeping raw passwords on the platform should be avoided. Application developers should avoid any storage of passwords, whether encrypted through hashing or not. After successful login, save an auth token with a short expiration (such as OAuth access tokens or JWTs) securely in the device’s storage. iOS devices and Android systems possess functionality related to this matter:
- The application should provide users with biometric login features for enhanced convenience and security. The iOS platform allows users to authorize app entry through Face ID as well as Touch ID, since Keychain provides biometric authorization for specific items, while Android supports BiometricPrompt for device and face authentication when confirming app entry or sensitive operations. The security implementation uses passwords or tokens as the base, but extends the protection with another authentication step.
- Passkeys, along with federated login methods, should be adopted by users whenever they become available. The newly emerging passkeys function as device-based passwordless authentication to provide a safer alternative to passwords. The latest version of Android Credential Manager now supports passkeys as its secure, user-friendly authentication method, while iOS/Safari users can also use this technology. When users sign in with Apple/Google/Facebook, they can delegate their authentication security to these providers while reducing their password-related exhaustion.
- Each app must access only its designated data by default through platform sandboxing features, which provide user data protection. Your app needs only essential device permissions, and platform security APIs serve as the proper storage solutions for private user information. Sensitive personal information, along with tokens, must not be saved as plain text in preferences or files. The secure storage methods for Android developers include private internal storage together with encrypted prefs, and iOS developers should employ Keychain or encrypted files as secure storage solutions. Users must receive secure authentication before developers protect data by isolating it within the device.
For more insights on advanced authentication, read Strong Authentication in FinTech and Continuous Authentication.
Network & API Security
All API calls and backend integrations need encryption. Due to their vital importance, mobile applications must protect their numerous backend API communication channels.
Experience the Power of Custom Software Development
Transformative Software Solutions for Your Business Needs
Explore Custom Software- Use HTTPS for all API traffic: This protection measure is of the utmost importance as it mandates the use of TLS for app-server communication. The complete lack of encryption in public Wi-Fi and carrier networks makes transit encryption an absolute requirement. The HTTPS process is straightforward for both iOS and Android platforms, so maintain new standards by refraining from legacy HTTP protocols or WebSocket vulnerabilities.
- API Authentication & Authorization: Mobile applications should only receive authentication services that the mobile environment cannot observe because its traffic is exposed to attack. The server needs to verify valid OAuth tokens and API keys before each request enters the system, and they should be validated directly on the server itself. Raw secrets should never be included in your application binary. A third-party API key used by your application should not be stored in plain text format. The secret should be protected through storage procedures involving post-authorization data retrieval or encryption. The protection of API keys must be maintained by avoiding source control submission and non-exposure during shipping processes. API keys must be stored in Keystore/Keychain while the mobile app maintains endpoint whitelisting rules or user-specific keys through backend restrictions.
- Input Validation & Avoiding Injection: Despite controlling the mobile client, you should never trust any incoming input because it can lead to injection vulnerabilities. Your system requires the validation and sanitization of all user-provided data that approaches your APIs and database. These safety measures ensure your services avoid disruptions caused by malformed data or injection attacks.
- Certificate Validation & Pinning: The HTTPS protocol performs default certificate validation to confirm that an authorized entity signed the server certificate. For high-security needs, adding certificate pinning, through which your app trusts only explicit certificates or public keys, becomes necessary. This security measure is a barrier against attackers who gain unauthorized access to fraudulent certificates. IOS and Android platforms provide support for pinning either through URLSession challenges for iOS or Network Security Config or manual check for Android. Apply pinning moderately because it will increase security and trigger app certificate updates.
- Backend Security Practices: To protect against abuse following mobile credential compromise, servers should implement both rate limiting and authentication tokens as security back-end practices. Any confidential information should be removed from the app code since mobile applications can be reverse-engineered. All important computations and decisions should be performed on the server system rather than inside the application.
Performance Optimization (Speed, Battery, Responsiveness)

A slow application, along with poor battery performance, generates hostility among both end-users and QA testers. The following guidelines will help you maintain an efficient and quick mobile application:
Optimize App Launch
Users experience better interaction when they get an application launch speed under two seconds. During startup time, it is crucial to delay all operations that are not fundamental to system functionality. Put off essential data and display elements until the opening screen loads before executing heavy initializations once the first frame becomes visible. Delay the execution of fetching user data and complex database migration processes until those processes become necessary. iOS and Android systems let developers measure cold start time through Android Profiler and Xcode’s Launch Time instrument.
Keep the UI Thread Free
The main thread of mobile UIs requires complete responsiveness to both touch inputs and animations. Major thread performance improves when users move expensive operations to separate threads. Android developers should execute tasks like networking or database operations with WorkManager while using background threads or Kotlin coroutines for this purpose. Device users should perform their resource-intensive computations with Grand Central Dispatch (GCD) or OperationQueue on iOS platforms. Operating database or file I/O on the UI thread will cause jank to happen. Large widget tree construction and build method synchronization should be avoided in Flutter because small chunks of work or isolated processing can improve performance.
Cache and Compress Data: Caching
Performance and offline support come from having a cache as your performance ally. Save data that users access often in the local storage to prevent continuous network requests from the application. The cache of selective API data (user profiles and static content) should be stored locally through databases or disk-based caches. Local data caching improves both data retrieval performance and eliminates power-consuming network requests. The storage of cached data must include an eviction system based on time or storage capacity to prevent displaying outdated information and storage space overflow. To improve app performance, ensure you optimize media file assets because big images and videos result in decreased speed. Apply image resizing to match use requirements in the app and implement file compression to minimize file size while maintaining acceptable quality levels. The optimization of page loading time, along with a reduction in memory usage, becomes possible.
Mind the Battery
It is designed for energy efficiency because mobile devices possess restricted battery power. The application should reduce background operations instead of conducting server polls every minute, since push alerts and extended sync times deliver better results. Program background operations through the OS’s JobScheduler/WorkManager mechanism (Android) or background fetch (iOS) to perform intelligent batching of tasks based on system recommendations. Test your mobile app battery performance through the Battery Historian of Android and Xcode’s Energy Gauge. Examine power-consuming features like GPS and heavy CPU usage because modifying or blocking their functions may result in better battery performance. Multiple device and operating system testing is essential for discovering battery-related and performance problems since different combinations might reveal distinct issues. According to a testing guide, it becomes possible to find out through multiple device testing how quickly your app drains the battery on a specific device compared to other devices, because you can address such issues before users begin to experience them.
Smooth and Responsive UI
Based on contemporary screen technology, strive to maintain a constant high frame rate, which should reach either 60fps or 120fps. Each frame should execute work before exceeding the 16ms time limit. A layout overdraw occurs when you duplicate drawing the same pixel multiple times, which Android Studio and Xcode can analyze through their visual tools. GPU acceleration should be used for all UI elements, while developers must prevent main thread delays from background processing (network calls should be handled asynchronously). Flutter users can deploy the Flutter DevTools performance timeline to detect dropped frames and slow widget builds.
Enhance User Experience with Our UX/UI Design Services
Crafting User-Centered Designs That Enhance Engagement and Maximize Conversions
Discover UI/UX DesignMemory Management
The combination of memory leaks and high memory consumption will result in slow application performance, which can lead to the operating system forcing the termination of apps. Users should utilize Instruments for iOS and Android Profiler for memory monitoring purposes. Free large objects through reference resets for situations when they are no longer required, and maintain awareness of image cache functions. The Dart VM memory management operates in Flutter, yet you must be attentive to big List<> data types and image storage.
Gain additional insights by reviewing Performance Testing in Software Development.
Crash Resilience & Error Handling
Applications possess characteristics similar to vehicles since they remain prone to incidents regardless of testing efforts. The system aims to minimize all possible crashes while providing smooth error handling during system failures.
Defensive Coding
Help your development team identify rare conditions in their work. The system must validate all incoming user data and server feedback. A proper application response requires developers to handle null or malformed data from APIs instead of permitting the application to crash. Put try/catch blocks (Swift uses do/catch for the same purpose) around operations that pose risks such as JSON parsing, database transactions, or file I/O. A network request should never be taken for granted, so always create error callback handlers or catch errors before showing user-friendly messages instead of letting the application freeze.
Graceful Degradation
The application must fail gracefully instead of causing complete system breakdowns during errors. The application should present an alternative placeholder when images cannot be displayed. A feature should display an informative message with an optional retry option when its service becomes unavailable. The application should inform users that data failed to load through feedback messages. Users need to pull the screen for a retry instead of facing an empty display. The quality of how errors are handled becomes a core element of the user experience because it presents valuable information to users as errors occur. Users prefer to see detailed error messages that help them rather than receiving weird system crashes.
Crash Resistance
Global exception handlers serve as safeguards against crashes. On Android devices, you can set an UncaughtExceptionHandler as the default to capture application crashes that bypass the system. Still, it will restart the app after catching them while enabling state saving and logging. Managed code within iOS allows you to see certain exceptions, while signals and multiple iOS crashes (including EXC_BAD_ACCESS) remain beyond managed code capture, which requires using crash reporting tools. A Flutter app can use runZonedGuarded to capture Dart exceptions, but it should combine this with FlutterError.onError to handle framework-level errors for logging and recovery purposes. The application must be built with transaction-based database writing to keep user data intact even when a background service crashes.
Testing & QA
A solid testing approach enables the detection of numerous crashes during the development cycle. The testing process should incorporate unit tests, integration tests, and manual exploratory testing. Basic flows within applications can be tested automatically through XCTest for iOS, Espresso for Android, and Flutter integration tests. The testing process should include evaluations of extreme situations, including weak network performance, which can be replicated with network link conditioners, and low memory situations. The number of issues detected during QA directly correlates with the number of bugs users will encounter. However, actual crashes may occur, so monitoring systems remain essential.
Monitoring, Logging & Observability
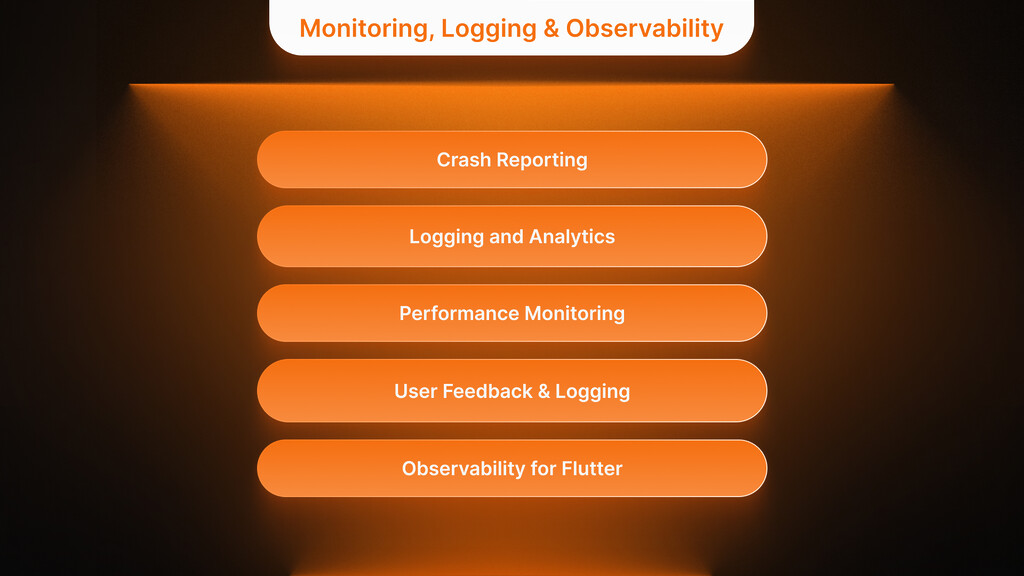
The delivery of your app to the market demands both performance observation and health monitoring techniques. From the first day of development, include monitoring and logging systems that serve as protection, detect problems quickly, and track user interactions in real time.
Crash Reporting
A crash reporting service should be used to gather error reports and crash logs from user devices automatically. The best crash reporting tools available on the market include Firebase Crashlytics, Sentry, Bugsnag, and other similar solutions. The SDKs provide application integration that automatically reports crashes, stack traces, device information, and operating system version to a monitoring dashboard. Such tools show you precisely where crashes originate and which devices affect most. Sentry and Bugsnag allow you to monitor error rates alongside trend analysis while offering analysis capabilities based on application version, device model, operating system version, and user geographical location, among other metrics. Using Crashlytics lets you track which crashes occur exclusively on Android 12 or iPhone 14 devices. The platform also detects velocity changes after releases and generates alerts. Your team will instantly receive notification about critical crashes through alert systems activated after new updates.
Logging and Analytics
The app requires app logging tools for debugging purposes and usage analytics instruments to gather insights. The practice of using logs for debugging purposes is acceptable during development. Still, excessive logging should be avoided post-release since it creates performance slowdowns and floods the logcat or device console. The system should only log essential events, warnings, and system errors. Maintain a policy against storing sensitive information since this would compromise user privacy. The tracking system should log analytic events to monitor performance metrics and user experience as users perform actions, such as when a certain task fails or a screen load time exceeds expected ranges. Firebase Analytics or Mixpanel enables this capability to alert developers about issues by tracking events such as checkout_failed spikes, which can indicate payment difficulties.
Performance Monitoring
Observability isn’t just about crashes. Production performance monitoring is an equally important task that you should conduct. The tracking capabilities of solutions like Firebase Performance Monitoring, New Relic Mobile, and Datadog enable monitoring of API call latency, screen render times, and UI hangs, which occur in the field. Firebase Performance automatically measures network request times and app startup time from users’ devices, which enables detection of persistent API slowness affecting particular regions and helps identify the performance impact of recent releases. Your monitoring system becomes more effective when you integrate these performance indicators, which show how applications function from the user experience standpoint beyond crash statistics.
Leading Research & Development for Your Success
Driving Innovation in Every Product Aspect Through R&D-Driven Software
Learn About R&D ServicesUser Feedback & Logging
App performance improves when direct feedback systems are implemented within the application. Teams often build their SDK implementations with Instabug and maintain “Report a problem” direct feedback features within their applications. With this system, users can submit reports and logs about bugs, which detect problems that prevent crashes if users encounter bugs or logical errors without causing a system crash.
Observability for Flutter
Your monitoring solution must track Flutter and other cross-platform system levels in addition to native components. The monitoring tools Crashlytics and Sentry provide integrated support for Dart errors and native crashes within Flutter applications. Check that your initializations are correct because improper setup will result in missing errors. Developers should employ Flutter’s dev tools to monitor their applications in real time during development, as the timeline and memory tools can aid the detection of performance problems at an early stage.
Find out more in the Ultimate Guide to Building Enterprise Mobile Apps with Flutter.
Update & Patching Strategies
The life cycle of an app includes updates as a necessary step, which affects both reliability and user trust levels. The proper process for updating applications results in quick bug fixes alongside minimal introduction of unexpected new issues. Key strategies:
Regular Updates & Maintenance
Support a practice of conducting consistent application updates. The maintenance of third-party libraries and SDKs with security updates requires immediate update deployment to users who need new OS support and bug fixes. Multiple smaller updates are preferable to a few large updates because identifying problems becomes easier while the overall risk remains low. Your continuous integration and delivery pipeline (CI/CD) should maintain automated development processes to deliver new updates instantly after testing.
Staged Rollouts / Phased Release
The App Stores from Google Play and Apple provide functionality to deploy updates to their user base in stages. One should avoid rolling out an update to every user base in a single release. The release process becomes safer when implemented through staged deployment, which starts with 5% user access, followed by two-day monitoring, then expanding to 20%, then increasing to 50%, and more. The staged rollout strategy enables you to limit the number of users affected by any escaping bugs, while you can stop the release process. An experienced developer explained that developers should not release updates without monitoring performance because monitoring during working hours remains essential. All user base deployments should start with staged percentage releases instead of an immediate full rollout. When you use staged rollout, you can remove updates containing problems to prevent most users from encountering them.
Discover more details about The Importance of Performance Testing in Software Testing Runs.
Feature Flags & Kill Switches
The system should enable administrators to activate or deactivate specific features through remote commands. The feature flag system developed by your team alongside Firebase Remote Config and LaunchDarkly provides an option to turn on or off different app features while avoiding the necessity of updating the application. New features that trigger crashes can be disabled through remote flags, which helps maintain stability before developers fix the issues and release patches to users. Users experience no problems with crashing in their chat session because enabling a new glitchy feature flag will automatically disable it for all members until a fix has been applied.
Fast-Track Critical Fixes
When serious bugs combined with security vulnerabilities surface, time becomes the main priority. The emergency plan starts with fixing what matters, then requires thorough testing of the issue and its solution before releasing updates as soon as possible. Apple’s App Store enables fast review processes for critical bug fixes, which you should use for major problems. Google Play enables approved updates to become available for users within a few hours. The release notes should include a clear statement about fixing the login crash issue to inform users about updating their app.
Patching and Legacy Support
Determine the period for which you will maintain support for past app versions. A general recommendation points toward motivating users to keep updated versions for new features alongside security updates. Users who run outdated versions of your app should receive in-app update notifications when possible, mainly when their version contains known issues. Server support for incompatible, outdated app versions might be disabled remotely only when users receive enough warnings to force them toward an update. Preserve essential server functionality for two or more preceding app releases, even when implementing user update incentives, as not all users can perform immediate updates.
Automate What You Can
CI/CD pipelines should be utilized to create an automated mechanism for building your app, including testing and releasing it. The automation results in faster development cycles by minimizing human mistakes. Testing each build automatically helps discover obvious problems before releasing to app stores. The test suite automation and build distribution to TestFlight/Play Console can be performed through Bitrise, GitHub Actions, or Jenkins tools. Your ability to release patches quickly improves when your process becomes more efficient.
Offline Capabilities (Caching & Local Storage)
Users on mobile devices do not always keep their internet connections active, and network delays often reduce the quality of their experience. Implementing offline capabilities improves user experience and establishes itself as a market benefit while sustaining users operating under weak network conditions.
Offline Mode & Data Caching
Examine which features of your application function without internet, and implement data storage techniques. The minimum requirement should be to store recent server data and user information in local storage through a database or file system to maintain visibility of previous content after network disconnection. Apps like news services cache current articles, whereas sales platforms cache their product listings. Using SQLite databases on both iOS and Android platforms or Hive/SharedPreferences storage in Flutter provides quick data access and offline functionality. Mobile applications operate with an offline-first strategy, which provides data from local storage before automatic background updates.
Sync & Conflict Handling
The application should update all changed data after it reconnects to the internet. The system executes queued requests, such as offline messages, while sending them to the server and retrieves updates waiting to be pulled down. The system must provide offline data conflict resolution, determining the winner or the merger method when server data changes match user modifications. Data timestamps and versioning systems enable users to determine which changes have been made. Users should experience uninterrupted work without losing offline changes as the primary objective.
Local Storage Best Practices
Applications should use appropriate data storage systems according to the nature of their information. The best approach for handling structured data with relational connections is to use databases such as Core Data/SQLite/Room. Local JSON or binary files deliver sufficient storage when working with simple lists or documents. The storage of small user preference items should utilize SharedPreferences (Android) or UserDefaults (iOS). However, be cautious because this data is not encrypted, so sensitive material should be stored elsewhere. Implementing periodic cache maintenance ensures they do not expand without limit – you should develop strategies to remove or overwrite data from image and API caches at specific time intervals or when they reach predetermined sizes.
User Control & Transparency
Users should be able to enable data caching or receive notifications about the large data cache status. For example, the video application should allow users to download videos, while the news application can set an automatic download feature for preferred articles. The feature should be optional because the data size is large. Users of the New York Times app can choose content for offline reading before downloading it, while also seeing the timestamp of the last update. The user interface should display the offline status when relevant through banners or icons indicating no connection, and statements showing content update timestamps. Users understand that they see stored data instead of real-time information through this method.
Connectivity Handling
The system should trigger synchronizations and UI updates through network connection change detection on iOS and Android platforms. Following an internet connection restoration, you can enable an automatic refresh of vital data by the app. Perform all major data synchronizations only when users explicitly grant permission to use cellular data. The system should manage unpredictable network connections beyond simple online and offline monitoring. Applications must smoothly handle network slowdowns by displaying stored data while showing an alert to the user and stating that the app displays saved information because of the slow connection.
Offline Testing
Test your application’s offline performance intensively through a complete examination. The app requires network interruption testing through emulator tools to determine which features stop working. The application must not freeze during server unresponsiveness since it should wait until server timeouts occur before managing the situation. When the application starts without internet access, you must verify that users can perform useful functions or receive a polite notification. Users become frustrated when they encounter apps that display only a “No connection – try again” screen at launch. It is better to present any previous data than display nothing.
Security for Offline Data
User data, such as names and messages, stored in a cached form, requires protection from all users. Offline data storage does not prevent it from being sensitive information. The storage of personally identifiable information needs to be encrypted when local storage occurs, especially when working within financial or healthcare sectors. The Keychain/K provides cryptographic keys that protect SQLite database files when utilizing SQLCipher encryption. Data caching remains inaccessible to unauthorized users when the device gets lost or someone attempts to access the app’s sandbox.
Check out 12 UX Best Practices for Mobile Apps and PACMAD Model for Mobile App Usability on the HyperSense blog for related best practices.
Future-Proofing Your Mobile App Strategy: Build Smart, Secure, and Scalable
Mobile technologies are advancing at their fastest pace ever. Businesses should no longer treat mobile app security and performance as secondary considerations because users expect more, regulations are tightening, and threat risks are growing. The essential nature of security and performance measures needs to run through the complete life cycle of application development, starting with initial coding and ending with final distribution.
The principles in this digest provide a blueprint that helps startups create their first MVPs and enterprises transform their legacy systems. A mobile experience that users adore requires each essential factor, including encryption, authentication, API security, performance optimization, crash protection, observability features, and offline functionality.
Deploying these best practices extends beyond technical expertise because they require business-strategic thinking, collaborative teams, and deep knowledge of organizational goals. A company requiring professional software development assistance should work with a trusted partner.
Our company, Hypersense Software, creates business-specific mobile and web applications for clients across the United States. Collaborating senior engineers, architects, and UX experts with clients exists to create secure, high-performance, scalable solutions.
Streamlining Your Path to Effective Product Discovery
Make Your Ideas a Reality in Four Weeks with Our Results-Driven TechBoost Program
See Product Discovery ServicesYou can contact us now to plan a risk-free meeting to learn about the solutions we offer for turning your ideas into a secure, efficient, and stunning reality.
Key Takeaways
- End-to-End Encryption is Mandatory: Always use HTTPS for data in transit (platforms enforce, and encrypt sensitive data at rest using Keychain/Keystore or encrypted data.
- Robust Authentication & Secure Data: Implement modern auth (OAuth 2.0, federated logins, biometrics) to secure user access, and never store credentials or PII in plain text on the device. Use OS-provided secure storage for tokens and keys.
- Secure Your APIs: Don’t trust the client blindly – validate inputs, avoid hardcoding secrets in, and consider certificate pinning for critical conn. Protect API keys and rotate them if needed to limit damage from leaks.
- Optimize Performance Proactively: Speed and efficiency aren’t luxuries – they’re expected. Keep launch times low by deferring non-essential tasks, offloading heavy processing off the main cache frequently, and optimizing media (images). A faster app means happier users and less battery drain.
- Build Resilient Apps: Assume things will go wrong and code defensively. Handle errors gracefully with user-friendly messages instead of crashes. Test under various conditions (no network, low battery, low memory) to ensure the app adapts.
- Monitor Continuously: Insight is everything once your app is live. Use crash reporting and analytics tools to keep an eye on app health in re. Track crashes, errors, and performance metrics to catch issues early and understand how your app is truly performing for users in the field.
- Smart Release Strategy: Treat app releases with care. Roll out updates gradually and monitor – this way you can pull back a bad build before it affects everyone. Use feature flags to disable problematic features remotely when necessary. Keep your software and libraries updated for the latest security.
- Offline Matters: Design for spotty networks. By caching data and offering offline modes, you keep your app useful anytime, which users love. Just ensure you manage cached data wisely (refresh it, secure it, allow user control). Clear indicators of online/offline state go a long way in user satisfaction.
SME owners along with tech leads who adopt these best practices will produce mobile apps that combine rich features with superior robustness and performance. Your business will benefit from better user retention and higher app ratings and peace of mind because of secure and performant and resilient apps. Be proactive by learning new things and you will develop your applications successfully.