Infrastructure as Code (IaC) empowers businesses to quickly build, deploy, and manage applications through automated, secure, and efficient methods. Traditional manual infrastructure management has become obsolete, as system outages today result in significant revenue losses and operational disruptions. Organizations dedicated to delivering high-quality software solutions must adopt IaC to modernize their infrastructure development, deployment, and maintenance practices.
What is Infrastructure as Code (IaC)?
Infrastructure as Code (IaC) transforms IT infrastructure management into automated processes using machine-readable scripts or configuration files instead of relying on manual handling. Writing code to establish servers, networks, and infrastructure represents the basic definition of Infrastructure as Code. Utilizing declarative definitions through IaC tools allows you to specify your infrastructure requirements, which those tools then create and configure accordingly. Employing code instead of console navigation or ad-hoc command execution enables IaC to automatically create identical environments, preventing inconsistent manual setups known as snowflake servers. Infrastructure code exists in files that users can modify and share and in version control. Documenting infrastructure changes through code enhances repeatability in infrastructure management, thus reducing the likelihood of unplanned configuration drift or surprises in the future.
Why is IaC important?
With companies increasingly moving to cloud environments, IaC has emerged as the backbone of modern software deployment. According to industry research, organizations leveraging IaC see a 40% improvement in deployment efficiency and experience 70% fewer configuration-related failures.
System administrators and developers historically relied on manual processes to configure environments, which was slow and error-prone. Modern cloud services startups and teams need rapid deployment, making manual infrastructure management impractical. Infrastructure as Code (IaC) automates management, allowing scripts and pipelines to create complete environments for development, testing, and production in minutes. This approach reduces time and human errors, as tested code enables reliable environment replication. IaC also generates documentation automatically, providing a clear record of configurations.
Custom Software Development for a Competitive Edge
Build Unique Software Solutions with Our Expertise
Explore Custom SoftwareIaC is crucial for startup growth because it transforms infrastructure management into an automated process. It allows for the easy addition of servers, environment replication, and outage recovery through code execution rather than manual steps. This leads to standardized environments, quicker deployments, and better resource control. IaC is fundamental to modern DevOps practices, requiring infrastructure to be managed with the same rigor as code development. The following sections will explore the benefits of IaC, its implementation challenges, and strategies for successful deployment.
Benefits of Adopting IaC for Startups and Growing Businesses
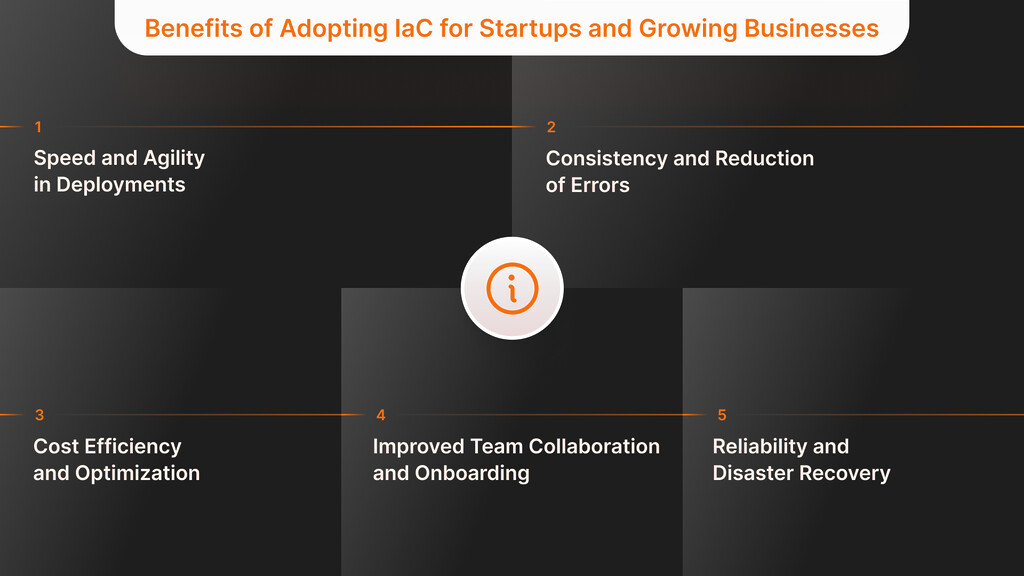
Modern systems management practices utilizing Infrastructure as Code implementations offer substantial benefits that improve technology performance and corporate results. Startups and rapidly growing companies gain significant advantages from IaC that revolutionize their operations. The following list outlines key benefits along with essential details:
Speed and Agility in Deployments
Through Infrastructure as Code (IaC) deployments, organizations achieve remarkable speed and agility in provisioning and modifying infrastructure. The deployment speed significantly improves through IaC methods, enabling the creation of new environments and modifications to existing ones in just minutes or hours. A code-based definition of the environment results in the automated and accelerated deployment of application stacks for new features, demonstrations, or increased demand requirements. Development teams achieve maximum efficiency due to environmental stability, as they waste fewer hours waiting and devote more time to delivering value. Development teams can apply their regular code pipeline by using Infrastructure as Code, accelerating delivery speed across infrastructure changes. This business practice leads to fast feature delivery while effectively responding to market demand. A startup gains a crucial market advantage through early product launches and rapid new feature deployment.
Development Teams for High-Impact Results
Strengthen Your Initiatives with Our Specialized Software Development Teams
Get Your Development TeamConsistency and Reduction of Errors
The manual practice of infrastructure updates leads to human errors and the gradual divergence of identical system environments—every infrastructure deployment through IaC results in systems with configurations previously verified as correct. Implementing code minimizes human error risks since the code that produced your staging environment last week will match the current deployment. Through consistent operation, every development stage replicates the exact configuration of the others, reducing instances where code functions on some systems but not others. The deployment reliability that IaC offers helps eliminate incorrect configurations while ensuring that the software maintains consistent performance across all contexts. Software code provisioning delivers more reliable results than manual setup tasks because it minimizes human errors. Fewer errors and mismatches contribute to a more stable product for your customers.
Cost Efficiency and Optimization
Through Infrastructure as Code, practitioners can achieve cost efficiency and operational optimization. Defining all resources within code, including servers, databases, and networking, enables better tracking of deployed resources while eliminating redundant, nonessential resources. With code-based management, organizations can identify unused resources for elimination and disable non-production environments during weekend downtimes. The ability to monitor and control cloud instances through this level of visibility helps organizations prevent unnecessary cloud costs from forgotten cases. Implementing auto-scaling and automated scheduling becomes possible through IaC. Startups benefit from IaC by optimizing their infrastructure deployment, deploying only essential components, and adapting quickly to the ideal infrastructure capacity. The complete tracking of resources in code enables better cost optimization and maintaining healthy margins through waste prevention since developers can more easily identify unnecessary resources.
Improved Team Collaboration and Onboarding
The entire team gains access to infrastructure configuration through Infrastructure as Code (IaC) since it resides in Git repositories. This breakdown of silos between operations and development allows everyone to view and review the infrastructure while users can propose changes that mirror application code access. The combination of DevOps culture and enhanced team collaboration is made possible through IaC methodology, simplifying onboarding for new team members. New engineering staff can study the infrastructure code to understand how the system was constructed. This code serves as its documentation system because standard definitions within the code eliminate the need for detailed setup manuals or verbal transmission of institutional knowledge. A CTO or technical leader should expect that when their single DevOps engineer takes time off or leaves the organization, others can maintain infrastructure management by examining the written code. The system employs shareable documentation that supports version control, reducing risk by not relying on memory or the expertise of a single individual to manage essential components.
Leading Research & Development for Your Success
Driving Innovation in Every Product Aspect Through R&D-Driven Software
Learn About R&D ServicesReliability and Disaster Recovery
IaC can rebuild environments anytime, automatically enhancing system reliability and disaster recovery capabilities. You can restore an environment by re-provisioning it from the original code when it fails to function correctly. The processes of backing up and recovery can be converted into code. The ability to quickly restart environments after worst-case scenarios becomes possible because of this approach. Startups without large operations teams or disaster recovery planners can establish high resiliency by implementing cloud automation and infrastructure as code practices. All systems become code-based, making rebuilding operations quick and efficient. The automated nature of infrastructure as code enables smooth expansion into new regions and duplicate environments for new customers, which supports business expansion without requiring additional manual work.
The numerous advantages highlight why modern infrastructure management views IaC as a fundamental support system. A startup or growing business can rapidly develop with IaC because it ensures automated speed and proven deployment reliability. Infrastructure becomes an adaptable resource through IaC, allowing business needs to dictate its size and shape independently of human assistance. Successful technology companies utilize IaC as a management tool for scaling, enabling small teams to manage large user bases through automated code implementations. The following section explores the implementation challenges of IaC, as its advantages are compelling, but execution requires careful attention.
Challenges and Potential Pitfalls of Implementing IaC
The numerous benefits of Infrastructure as Code do not simplify its implementation process. Adopting IaC presents challenges and typical obstacles that may hinder teams with limited experience. By identifying these implementation issues, you can develop better strategies for your startup’s IaC adoption. Highlight the primary difficulties along with their solutions.
Initial Learning Curve and Cultural Shift
The IaC approach requires team members to master new solutions while adjusting their infrastructure mindset. Learning Terraform scripts that operate through its configuration language and CloudFormation templates presents challenges for users who rely on cloud console clicks. Companies must initially invest in training staff and conducting experiments as part of the development process. The cultural shift involves bringing developers together with operations personnel (DevOps culture) to ensure the success of infrastructure as code practices. Some team members resist abandoning their established manual operating procedures. A basic understanding of equipment and participation in smaller test projects enhance users’ proficiency. Team members require organizational support to navigate their learning curve, with the CTO’s endorsement of automated methodologies and potential adjustments to team procedures.
Choosing the Wrong Tool or Framework
The large number of available Infrastructure as Code tools creates the risk of selecting an unsuitable one, which can lead to future complications. A common error occurs when users limit themselves to tools from a single cloud platform. Implementing AWS CloudFormation and Azure Resource Manager templates creates IaC dependencies that function correctly only within their respective cloud provider formats. Reusing templates designed for a single cloud provider becomes challenging when multi-cloud usage or provider changes are necessary. The initial cloud deployment of a startup typically begins on a single platform, but business demands may later require both multi-cloud and cloud migration deployments.
Selecting cloud-agnostic Infrastructure as Code tools such as Terraform or Pulumi becomes essential when operators want to avoid being locked into one specific provider, as these tools support multiple providers. Choose IaC tools from the outset that do not restrict your cloud options; evaluate your future cloud requirements for multi-cloud flexibility. The decision between cloud-specific tools (such as CloudFormation and Azure’s Bicep) may be more straightforward for monolithic cloud projects, although these services offer less flexibility than cloud-agnostic tools. Teams must carefully consider their deployment needs before making a decision.
Web Development for a Strong Digital Foundation
Build a Robust Online Platform with Our Expertise
Discover Web DevelopmentInsufficient Collaboration Between Dev and Ops
IaC serves as the common area that connects development work with operations tasks. Many organizations mistakenly view IaC as a responsibility of only one team. The results become suboptimal when IaC developers work in isolation without consulting operations or infrastructure engineers (and vice versa). A developer may create inefficient resource deployments that overlook networking complexities, while an ops engineer might code solutions that struggle to align with development methodologies.
The success of IaC relies on collaboration between developer and operations teams or their integration into a single DevOps team for planning and implementation. Ops experts provide recommendations on capacity planning, security, and governance, while developers ensure the IaC integrates properly with application delivery pipelines. Operational issues, such as insufficient scalability and complicated deployment procedures, can arise when developers and operational staff fail to collaborate on infrastructure as code projects. Eliminating organizational silos and promoting shared IaC ownership reduces these security risks.
Security as an Afterthought
Writing infrastructure code without considering security poses a significant threat that should be avoided. Security configurations often take a backseat when developers prioritize system deployment. Database ports and secrets such as passwords or API keys can remain exposed to the world when developers mistakenly leave them open or hardcode them in IaC files. The primary goal of IaC is to identify security flaws during the early development phases rather than at later stages, where traditional security teams typically uncover misconfigurations before production deployment.
Startups must integrate security checks into the IaC process from its initial stages—Policy as Code tools implement automated checks that run whenever infrastructure code is set to deploy. Open Policy Agent (OPA) and HashiCorp Sentinel act as Policy as Code tools for enforcing security rules to ensure that no S3 bucket becomes publicly accessible. The main challenge lies in establishing these security measures requiring initial setup and staff understanding. Realizing your IaC misconfigurations only after experiencing a breach or compliance failure represents a significant risk. Security must be the top priority in your IaC workflow by integrating security requirements into the code, applying code review protocols, and selecting IaC vulnerability and misconfiguration detection tools.
Overlooking State and Environment Management
The deployment state file maintained by Infrastructure as Code (IaC) tools, including Terraform, tracks all deployed resources. A lack of proper management can transform this state into an infrastructure problem. The single state file that monitors your entire infrastructure becomes large, causing update processes to slow down or pose higher risks. Adding small changes to a state containing every resource becomes time-intensive, as it requires loading and checking all resources and carries the risk of losing state data, which can be a significant issue. Organizations encounter problems when they start with small projects but continuously add more projects to one state as they grow. Modularization and environmental separation resolve this issue.
The IaC configuration should encompass separate logical components, such as network settings in one module, databases in another, and application servers in a different module. When modifications occur to application servers, it allows infrastructure state changes without impacting other areas. Different environments need distinct state files and configuration sets to prevent environmental interference rather than combining everything into one extensive configuration. Implementing modules and independent workspaces or state backends helps minimize performance issues and contains damage spread when errors occur. Frontend design presents a challenge because proper planning of code organization at the outset leads to superior management capabilities.
Not Following DRY (Don’t Repeat Yourself) Principles
Infrastructure as code requires engineers to implement software development standards for IaC management at the same level they use for application code. Copying code across environments and components creates numerous similar blocks that become difficult to maintain. A single set of templates exists for your development deployment, while separate templates exist for production, with minor distinctions between them. The duplication process introduces potential errors because developers tend to forget to apply changes from one environment to another.
The elimination of repeated code depends heavily on parameters, variables, and modules. Multiple tools and standardized patterns exist to assist with this task. Within Terraform, you can achieve this objective through variables to personalize one template across different contexts, while Terragrunt provides an interface that enables code reuse across environments. The main risk occurs when you discover duplicate IaC code in other locations, indicating that you should convert it into reusable modules or templates. Such an approach will protect your time by saving your work in the future and will reduce the number of errors you make.
Tooling and Integration Challenges
Integrating IaC into workflows leads to practical challenges, including secret management, CI/CD pipeline integration, and rollback management. Storing sensitive information, such as API keys and passwords, in your code repository poses a significant security risk, even though your IaC requires access to these elements for resource provisioning. Your IaC system should connect to secret management platforms instead of exposing secrets in plain view. Proper configuration of this step is an additional requirement, which can lead to security issues when overlooked (we will discuss this further under security). Your CI/CD pipeline needs to be correctly configured to ensure the safe deployment of IaC changes through staging environments or by executing the Terraform plan (for Terraform) before actual implementation. Neglecting these aspects will result in deployment problems due to misconfigured changes.
IaC’s benefits to infrastructure management require you to establish proper planning and best practicesduring the initial implementation. Implementing IaC can become counterproductive due to cloud vendor lock-in, lack of collaboration, insufficient security oversight, unmanageable configurations, and duplicated code. The industry has gained valuable insights from early adopters, enabling you to avoid most IaC implementation difficulties when you create your approach with proper foresight. Terraform stands out from other available IaC tools, which we will analyze in the next section.
Key IaC Tools and Technologies (with a Focus on Terraform)
Multiple widely used tools exist for implementing Infrastructure as Code. The best tool depends on your particular needs because different tools excel in other areas and match different requirements (such as cloud provider, team expertise, and desired outcomes). This overview introduces essential infrastructure-as-code tools, emphasizing Terraform, which many startups and enterprises select as their primary solution.
Terraform (by HashiCorp)
Terraform is an open-source infrastructure-as-code tool that enterprises from multiple industries have adopted on a large scale. The HashiCorp Configuration Language (HCL) allows users to create cloud and on-premises resources through human-readable configuration files. Terraform operates across all cloud environments, providing AWS, Azure, and Google Cloud Platform providers and non-cloud services such as Kubernetes, GitHub, and Datadog. This approach lets users handle all their infrastructure elements from a single centralized platform.
Users define their infrastructure state by writing with Terraform, automatically creating the necessary updates or deleting resources to match that state. The configuration files allow Git versioning, sharing, and reuse, which enhances teamwork. Terraform’s “plan and apply” process lets users preview changes before deployment, making the system safer. The state file maintained by Terraform tracks infrastructure status, allowing the system to perform efficient incremental resource management without needing a complete rebuild process.
Terraform is a primary infrastructure-as-code tool that enjoys worldwide acceptance. It has extensive community backing, many pre-built modules, and multiple providers. In 2023, the number of Terraform providers reached 3,000, while its published module library exceeded 12,000. Thousands of production companies have utilized Terraform for their work. Terraform’s widespread popularity provides new infrastructure-as-code teams with a strong community network, abundant examples, and multiple integrations, making it an appealing solution.
Cloud-Specific IaC Tools
The major cloud providers operate independent Infrastructure as Code (IaC) solutions. AWS features CloudFormation and its newer Cloud Development Kit, called AWS CDK. Azure provides ARM (Azure Resource Manager) templates and Bicep, while Google Cloud operates Deployment Manager. These tools specifically function with their native cloud infrastructures. CloudFormation implements resource descriptions through JSON or YAML templates. The systems offer maximum power when your organization entirely depends on a single cloud platform because providers maintain and instantly support new services.
The major drawback of these templates is their inability to transfer between different cloud platforms. AWS CDK provides developers with an interesting feature that enables the creation of infrastructure code using standard programming languages like TypeScript, Python, and Java, which automatically converts into CloudFormation templates. This method allows teams to utilize standard development tools. The CDK sees widespread adoption because developers can use familiar programming languages to access cloud configuration through code. The Bicep language from Azure provides developers with a superior modular approach to creating Azure resources developed from JSON templates.
Configuration Management and Other IaC Tools
The rise of cloud provisioning using Infrastructure as Code (IaC) terminology emerged after tools such as Chef, Puppet, and Ansible had already been established for configuration management. IaC tools entered the market to assist users in setting up software deployments and configuring servers, and they later expanded their capabilities to manage cloud resources as well. The IaC tool Ansible allows users to create cloud infrastructure deployments through SSH/API calls without establishing agents on managed systems. In contrast, Chef and Puppet function through agents, each implementing its native configuration languages. Terraform often works with Ansible to manage server deployment processes, where Terraform creates the servers, followed by Ansible handling the software installation tasks. Together, these tools form an essential part of studying the IaC landscape.
The practice of IaC extends beyond just cloud resources, as it necessitates proper server configuration, also known as configuration as code. In cloud-centric environments, provisioning responsibilities primarily fall to Terraform, whereas Ansible deals with configuration tasks once provisioning is complete. Additionally, the configuration tool SaltStack joins the ranks of notable tools alongside newer orchestration systems from Kubernetes, such as Helm, which enables Kubernetes resource configuration management. Companies operate across a continuum encompassing server configuration tools (Ansible, Chef, Puppet, SaltStack) and infrastructure provisioning tools (Terraform, CloudFormation, etc.), with most organizations implementing both types.
Pulumi
Pulumi’s approach differs from traditional Infrastructure as Code (IaC) tools because it allows users to define infrastructure using generalized programming languages such as TypeScript, Python, Go, and C#. Developer-heavy teams find Pulumi particularly appealing, as this tool enables them to write infrastructure definitions with standard programming constructs like loops, conditionals, functions, and package management. With Pulumi, you can develop an AWS resource creation program in TypeScript, and Pulumi will manage the deployment process.
Using Pulumi allows developers unfamiliar with Terraform syntax to bridge application and infrastructure code more efficiently, enhancing productivity. Using common languages, Pulumi establishes a connection between development and operations tasks. The main drawback of Pulumi is the increased code complexity, as users must manage programming dependencies and projects, while Terraform users benefit from a more straightforward declarative configuration. Nevertheless, Pulumi offers significant advantages for complex scenarios and teams of software engineers.
Other Notable Trends/ Tools
Kubernetes-focused IaC emerged with Kubernetes popularity because Helm charts and Kubernetes manifests (managed by GitOps tools like Argo CD or Flux) constitute Infrastructure as Code for deploying applications in Kubernetes clusters. The emerging tool Crossplane allows Kubernetes to serve as a platform for provisioning cloud infrastructure, enabling users to manage their cloud resources through Kubernetes APIs. Team-oriented Terraform Enterprise/Cloud solutions offer built-in state storage, policy enforcement, and collaboration features, which become essential as IaC usage grows within teams.
Our discussion will focus on Terraform, as it serves as the primary illustration. Startups choose Terraform because it offers multi-cloud capabilities, a large user base, and strong product stability. With Terraform, developers can create a unified configuration that builds AWS infrastructure while setting up Cloudflare DNS and monitoring dashboards within the same tool. The tool’s ability to operate across multiple cloud environments provides a significant advantage. Terraform configurations and similar tools utilize text files, enabling you to leverage standard software practices, including code reviews, Git version tracking, reusable modules, and automated code testing. Startups gain from HashiCorp’s Terraform Cloud platform, which operates Terraform as a collaborative service that manages remote state and team permissions, offering a viable alternative to self-hosted infrastructure.
The implementation of IaC involves multiple possible approaches. For new startups, the standard IaC implementation starts with Terraform for cloud resource provisioning, while Ansible manages server configuration needs, and all IaC code resides in a collaborative repository. As your organization grows, you can evaluate more sophisticated solutions, including Pulumi for Python developers, Terraform Cloud to enhance team capabilities, and CloudFormation for AWS-specific tight integration. Every Infrastructure as Code tool embodies the fundamental concept that infrastructure specifications should exist as code rather than rely on human memory or one-time scripts. In the next section, we will cover best practices for maximizing the potential of your chosen IaC tool.
Best Practices for Successful IaC Implementation
The effective deployment of Infrastructure as Code solutions depends considerably on how you utilize IaC tools rather than the tools themselves. Startups and their teams need to follow these best practices for Infrastructure as Code deployments to achieve effective results while maintaining system safety and maintainability:
Treat IaC Like Application Code (Use Version Control and CI/CD)
Infrastructural code should be stored in a version control system like Git, which functions similarly to standard application code storage. This system enables multiple developers to collaborate through code reviews, maintain an audit trail to track history, and allow easy reversions when mistakes occur. The proposed Infrastructure as Code (IaC) changes must undergo a code review process, requiring at least one team member with infrastructure expertise to examine the modifications.
This review process facilitates the detection of mistakes and unforeseen results. Implementing CI/CD pipelines for IaC includes automatic Terraform plan executions on pull requests, displaying changes, and may require approval specifically for database deletion operations. When IaC is version-controlled, you gain complete traceability, as you can quickly identify who made changes, what modifications were made, and when they occurred. This method enables the capability to revert to established configuration states.
Modularize Your Infrastructure Code
The configuration should not exist as a single, massive, monolithic entity. Organize your IaC into distinct modules and separate templates representing natural components like network, database, and application modules. Reusing modules is beneficial when you need duplicate environments, allowing you to apply the same module structure with different configuration parameters. This modular structure enhances the understanding of complex systems and simplifies comprehension. To achieve composition, startups with multiple products or microservices should divide their infrastructure-as-code solutions into separate modules. The modular structure improves performance by reducing state scope and minimizing the risk of unintentional changes to unrelated infrastructure components. Most infrastructure-as-code tools provide modules and include capabilities you should leverage to maintain DRY and organized configurations.
Use Descriptive Naming and Tagging
Every resource in IaC should adhere to a standardized naming system. Defining resources with clear names is crucial for you and your team during cloud console inspections and billing verifications. A resource description like “web-server-serv-us-west-1” offers better clarity than “server987”. Tagging and labeling resources is possible using tags combining project names with environment (dev/test/prod) identifiers and team ownership labels. Tags serve two primary functions in managing costs while simplifying resource management. Security audits also benefit from tags, as they provide insights into the existing aspects of the infrastructure. Most organizations implement IaC to establish tagging requirements, mandating that all resources possess both cost-center and environment-specific tags. Proper tagging of all resources ensures that unwanted, abandoned resources remain visible, avoiding unnecessary financial costs and security risks.
Avoid Hardcoding and Use Variables/Parameters
You should avoid embedding core values, such as server sizes and IP addresses, into your code base and instead adopt a variable-based approach for content injection. With input variables, you can use a single code block across multiple situations by only adjusting variables. You should create a single Terraform application stack module that accepts the number of servers and instance types as input variables, allowing the production deployment to differ from the development deployment.
Avoiding hardcoded secrets or environment-specific content helps prevent code duplication and mistakes. Different environment-specific variables in variable and configuration files enable the core code to remain identical and prevent environment misalignment. Adjusted settings become more manageable because you only need to alter one variable value instead of using find-and-replace across multiple lines of code. The main feature of any Infrastructure as Code framework is parameterization support, which you should utilize.
Implement Secret Management
IaC code and repositories must never contain secrets by best practices. The best practice for securing secrets involves using secret management solutions. Utilize cloud services alongside tools to reference secure storage and facilitate runtime secret injection. Terraform files should not store database passwords; they should be kept in AWS Secrets Manager or HashiCorp Vault, allowing your IaC tool to retrieve them securely during execution. IaC tools enable users to access encrypted values or environment variables as secret storage options.
Following this approach helps maintain data security and comply with regulatory requirements concerning customer information storage. Systems or pipelines requiring access to secrets should only be granted permission to retrieve them. Plaintext passwords or keys remain inaccessible to unauthorized parties due to the protection offered by your code repository. Including secrets within code presents a significant risk because they can be leaked or misused, so design your IaC process to eliminate secrets from the codebase.
Plan for Environments (Dev/Staging/Prod)
Your IaC design must include features that enable quick and easy environment deployment. Organizations typically arrange their environments into separate directories or workspaces or apply different variable files to the same module definitions across environments. A development environment designed for testing purposes must exactly replicate the production system. Placing these definitions next to each other highlights their distinct characteristics. Your code should incorporate naming conventions that differentiate various environments through unique names.
Separate back-end state files or different cloud accounts and projects should be utilized for segregation if necessary. Changes in the development environment should avoid unintentionally impacting the production environment. Early strategy planning for environment development remains crucial because splitting one large environment into three becomes extremely difficult to reverse. The pipeline for promoting changes becomes clearer when definitions establish dev/staging/prod boundaries, allowing you to advance code changes from development to testing to production. This strategy benefits product managers and QA engineers, as they can work with realistic environments while minimizing issues from staging built from the same codebase as production.
Test Your Infrastructure Code
Testing IaC should be conducted in the same way as application code testing. Most tools include code linting and validation features that provide commands for syntax checking and basic logical verification. Testing with Terratest allows for the deployment of miniature environments while verifying their state, and policy-as-code enables the establishment of specific requirements, such as mandates for S3 bucket encryption. A basic test of your changes can be performed through dry runs using a terraform plan or a similar tool alongside change reviews. Teams that support pull request testing deploy temporary test environments, which they create using IaC before destroying them; this provides strong evidence that the code functions correctly. Critical tests should be performed on your IaC components during code modifications (run the database module in a controlled environment to validate data protection against coding errors).
Continuous Integration & Delivery for IaC
Your IaC needs integration with a CI/CD pipeline. The infrastructure code requires a pipeline system to conduct minimal sanity checks (plan) while enabling automatic deployments to a testing environment. The implementation of automation prevents operators from overlooking essential steps by requiring manual approvals only for production changes. Security scans involving tfsec, Checkov, and AWS Config rules should be incorporated into the pipeline to identify potential issues before production deployment. CI/CD enforces consistent change processes since all deployments occur identically each time, preventing manual alterations that could compromise IaC. The system generates chronological records detailing modifications along with their timestamps and information about which automated processes enacted the changes. Your infrastructure code delivery should be given equal attention to application code delivery to achieve a mature implementation.
Use Policy as Code for Governance (if needed)
Your startup’s expansion and regulated business sectors may necessitate implementing infrastructure rules such as data encryption at rest and blocked ports according to policy. Your organization should integrate these rules into automated Policy as Code systems. Your infrastructure as a code tool employs written rules in code format to validate infrastructure definitions. The deployment process automatically fails when someone tries to create an unencrypted database resource through OPA or Checkov policy enforcement systems.
This approach exemplifies a best practice for compliance and security, eliminating the need for human involvement in complete detection. The initial implementation is more straightforward than performing retrofits later. Startups in fintech and health and enterprise sectors would reap maximum benefits from this strategy. Checkov is your infrastructure’s unit testing solution to prevent unintended deployments exceeding your established limits.
Document and Comment Your IaC (where necessary)
The self-documenting nature of IaC should be supported by adding README files or inline comments when dealing with complex setup sections. Note any dependencies or workarounds in the code that are not self-evident. A top-level README file that describes the repository structure with examples such as “module X creates the VPC and module Y handles the application cluster” helps newcomers understand the layout. The documentation should include information about both code execution and team processes, which encompass the IaC deployment procedure, change management protocols, and identification of responsible team members. Team coordination practices take precedence over technology implementation yet are essential for maintaining alignment across the team. Executives, alongside PMs, may not review code directly but might instead evaluate summary documents; therefore, create a one-page document with diagrams to present your infrastructure overview to non-technical stakeholders.
By implementing these best practices, your team will achieve Infrastructure as Code’s promised outcomes. The upcoming discussion will cover maintainability and scalability, which your setup enables. The objective of infrastructure code development is to establish code that performs reliably and securely and can be reused. Early investment in these habits by startups enables smooth scalability of systems and teams because infrastructure management stays organized during company growth.
Security Concerns Related to IaC and How to Mitigate Them

Any infrastructure strategy requires security, and Infrastructure as Code (IaC) presents both security advantages and challenges for system protection. IaC improves security through standardized and auditable configurations, yet security vulnerabilities can arise when the management of IaC lacks proper vigilance, potentially leading to resource exposure and secret leaks. This section discusses the vital security risks associated with IaC and proven defense methods.
Exposure of Secrets and Sensitive Data
Infrastructure as Code (IaC) security primarily relies on the risk of secret exposure when passwords and API keys are stored in plaintext within unsecured git repositories, especially those accessible to the public. Embedding secrets directly in IaC files should be avoided; placeholders that connect to secure secret management systems for runtime retrieval should be utilized. Proper protection includes limiting repository and pipeline access to essential personnel while implementing secret detection tools to identify unintentional exposures. The secure storage of state files necessitates placement in encrypted Amazon S3 buckets that use restricted IAM access controls. Handle your IaC artifacts in the same manner as production credentials because they have the potential to control your entire infrastructure.
Configuration Drift and Manual Changes
The primary security benefit of Infrastructure as Code (IaC) is its ability to prevent configuration drift between the defined code and the actual environment. The drawback occurs when personnel make manual changes outside the IaC process, as such actions can introduce security risks (for instance, an administrator might forget to close a port after a temporary modification).
A mandatory policy should be established requiring all changes to infrastructure to follow Infrastructure as Code procedures. In cases of emergencies, the IaC configuration must immediately reflect any manual changes made. Access to the production console is restricted by specific organizations that require changes to be implemented through code and utilize GitOps workflows. Drift detection tools allow organizations to identify any divergence from the IaC state, which is treated as bugs needing correction. The primary objective is maintaining immutable infrastructure to ensure auditability and consistency while reducing security incidents arising from untracked modifications.
Excessive Privileges (IAM and Access Management)
Security risks may appear when writing IaC because improper definitions of roles and permissions can lead to excessive access. The essential implementation of Least Privilege requires IAM roles and security groups to provide only crucial access levels. Cloud provider tools should help you detect excessive security policies in your infrastructure, and you should conduct regular reviews to check IaC security aspects. Policy-as-code automation boosts security by restricting the use of wildcard permissions. Enforcing the least privilege throughout your system reduces damage when credentials or resources become exposed.
Vulnerable Base Images or Components
Using machine images and pre-made modules within Infrastructure as Code (IaC) introduces security risks when they contain outdated components. Outdated virtual machine images do not receive necessary security updates, and utilizing community modules might lead to configuration errors. The security of your IaC relies on the proper monitoring of its components, as well as using trusted image sources and regularly updating them, similar to code dependency management. Conduct infrastructure vulnerability scans and use tools to detect risky configurations within your IaC code. Your deployment process should include automated checks that prevent high-risk vulnerabilities from completing deployments, enabling early problem detection.
Policy Compliance and Governance
Proper security and compliance measures are vital for your startup if it must adhere to HIPAA or GDPR regulations. Infrastructure as Code (IaC) enforces compliance rules through code-based implementation. The implementation process requires careful attention to avoid missing any requirements. A solution to mitigate this risk involves developers creating code tests and checklists based on compliance requirements. Compliance standards mandate encryption for all data storage; therefore, developers must ensure it is enabled. Resources that process sensitive data must be documented and tagged according to organizational policies. Cloud Custodian or Open Policy Agent can monitor real-time infrastructure compliance, which detects operational deviations. Infrastructure code audits against compliance checklists through automated processes identify issues in advance, leading to automated checks that would otherwise need manual verification.
Discover Our AI Integration Experts
Elevate Your Business with Advanced AI Integration Services
Access AI Integration SolutionsAccidental Resource Exposure
The main error developers make involves improper access configuration when enabling worldwide database access or leaving S3 buckets publicly accessible. Multiple resources are affected by errors when operating in an IaC environment. You should include guardrails in your codebase to enforce CIDR range limitations and IaC linting tools that detect standard security issues (such as S3 bucket public visibility alerts). Cloud provider config rules will help identify these problems when activated. Default-deny security measures should be employed, allowing only essential resources to be opened, and users must verify all examples obtained from internet sources. Peer reviews serve as an effective method to detect security exposures that occur by chance.
Security requirements should be integrated into your Infrastructure as Code (IaC) process. Employing the IaC methodology makes your infrastructure more manageable for enforcing security rules, as it facilitates infrastructure codification. Combining secure coding practices with automation tools and strict policies mitigates security risks. Making security integration a startup’s initial focus is crucial, as adding it after infrastructure development will pose more challenges. The main goal of Infrastructure as Code extends beyond automation; it also upholds security measures and compliance standards. Properly implementing this methodology incorporates security into the infrastructure, protecting against breaches resulting from system misconfigurations. When implementing rapid infrastructure changes through IaC, ensure their safety and intentionality. The following section will discuss how to manage and scale your IaC framework as your startup grows.
Maintainability and Scalability Considerations for Long-Term IaC Use
The Infrastructure as Code (IaC) setup requires scalability to support expansion in engineers and the growing complexity of requirements within your startup. The success of IaC depends on achieving operational success in one project and maintaining organizational structure during expansion. The following guidelines represent essential factors that help maintain and scale your Infrastructure as Code setup during its growth period:
Code Organization and Structure
The initial decision about repository and file organization remains crucial for developing smooth operations in IaC. The organization of IaC files should use a combination of environment categories (dev, staging, prod) with component sections (network, database, app) to avoid editing multiple separate files during changes. Effective organization in IaC code allows new team members to see system relationships and facilitates maintenance and troubleshooting operations. The management of IaC becomes complex when its structure fails to support simple changes and maintenance operations. Well-organized code enables easy updates across environments while simplifying onboarding and allowing compliance without any difficulties. A microservice or cloud region addition should be straightforward without needing large amounts of duplicated code.
Reusability and DRY at Scale
You will start identifying recurring patterns as you observe your infrastructure over time. The combination of ECS clusters, RDS databases, and IAM roles often appears in various microservices. The practice of duplicating infrastructure as code (IaC) should be replaced with reusable modules or templates. Module reuse enables faster component development, while maintenance becomes easier because fixing the module benefits all dependent services. Avoid excessive engineering, as generic templates can become complicated and challenging to maintain. Refactoring shared code remains acceptable when patterns begin to emerge. Develop an internal repository to store modules and encourage teams to enhance their content. This practice establishes an internal reusable IaC components system that operates alongside developer-specific standard libraries.
State and Configuration Management as You Scale
To eliminate conflicts, state files, and backend configurations for IaC must be managed using separate state backends between different environments and teams. State-locking systems should be implemented to prevent multiple users from creating unintended modifications. Your team’s growth requires you to enforce safeguards through pull request review systems that the central platform team should handle for production changes. Striking a proper equilibrium between governance structures and agile deployment methods will help organizations prevent confusing situations while staying productive.
Scalability of the IaC Processes
Your CI/CD system must demonstrate its ability to function at increased capacity. Slow application jobs caused by extensive infrastructure should be addressed through component breakdown or distributed parallel execution of Terraform. Understand API rate limitations for each tool since creating multiple resources may require dividing your application into sections. Optimizing your pipeline should include a mechanism to bypass linting and planning phases for remaining unchanged modules. Focus on these advanced concerns to manage growth effectively.
Documentation and Knowledge Sharing
Maintaining current documentation becomes vital as Infrastructure as Code (IaC) gains popularity, requiring the inclusion of code examples alongside operational guidelines like DNS entry creation. The platform and DevOps teams should organize sessions for developers to learn about IaC practices. The greater the number of team members collaborating, the more essential it is to follow standardized conventions to avoid conflicts. Implementing code reviews and providing detailed documentation on best practices and standard challenges are crucial for success. The “infrastructure cookbook” developed by some teams guides new members, accelerating their onboarding process while minimizing mistakes.
Evolving and Refactoring IaC
Your requirements will evolve over time due to new technological developments, such as Kubernetes or serverless components. Regularly refactoring your Infrastructure as Code (IaC) setup is vital. The code for deprecated services should be removed to uphold clarity. You should embrace better organizational opportunities and feature enhancements to your IaC tool while thoroughly performing and testing all migrations. Technical debt accumulates in Infrastructure as Code similar to application code. Implement regular schedules to manage module updates and simplify complex structures. When refactoring, treat it as an organized project by developing a plan followed by extensive testing in a secure environment before safe implementation. A clean Infrastructure as Code base reduces support needs and the likelihood of mistakes.
Scaling the Team vs. Scaling the Infrastructure
The management of Infrastructure as Code (IaC) typically begins with one or two initial personnel. As your organization grows, it will require multiple developers to modify the infrastructure code. At this stage, establishing a Platform Engineering or DevOps team becomes crucial for managing core infrastructure while developing golden templates that allow application developers to operate at a higher level while adhering to best practices. Due to its significant workload, startup infrastructure needs specialized personnel to create IaC-driven self-service tools.
An “Internal Developer Platform” provides developers with a straightforward interface for executing Infrastructure as Code operations. The team structure and ownership model must also evolve as your infrastructure scales, as what works for one DevOps engineer may not be suitable for larger teams. Enhanced collaboration in infrastructure code requires implementing tools like Terraform Cloud and Spacelift.
Developers should adhere to established software engineering principles to ensure maintainability and scalability in infrastructure as code (IaC). Keep your code organized and refactor as necessary while fostering team collaboration. A well-organized IaC structure enables teams to expand efficiently, utilizing proven code modules for new services. Strong IaC foundations allow companies to manage large infrastructures with smaller teams. Regularly assess your infrastructure code to support growth while maintaining clarity and effectiveness for scaling operations.
Application Lifecycle Management with IaC
IaC works alongside application development and deployment methods to realize its benefits. Fully implementing IaC leads to significant improvements in the application lifecycle management process, which extends from development to production. The implementation of IaC functions at various stages of the lifecycle through these practices:
Consistent Environments from Dev to Prod
Software development faces a recurring problem because different environments often create inconsistencies that lead to the “it worked on my machine” error. Infrastructure as Code (IaC) serves as a solution to establish uniform environments that extend from development through testing and staging to production. The same IaC templates enable developers to create a test environment closely resembling production, which helps prevent deployment surprises. This approach allows for testing configuration changes in lower environments before promoting them to production. DevOps practices depend on this consistency to unify development and operations while minimizing integration issues that arise.
Integration with CI/CD Pipelines
CI/CD pipelines today generally connect with infrastructure management practices. New application deployments enable the simultaneous delivery of infrastructure components, such as databases and queues, through Infrastructure as Code (IaC). The deployment process via the pipeline starts with automated testing, followed by container building, and then moves to IaC execution for infrastructure deployment, application deployment, and integration testing before progressing to the next environment. Integrating IaC allows for the simultaneous review and testing of infrastructure changes alongside code modifications, leading to shorter deployment times and fewer errors. The CI/CD process automatically generates infrastructure when developers specify their requirements in feature branches. Infrastructure changes become a critical part of the software release workflow through the IaC process.
Deployment Speed and Reliability
The deployment process speeds up significantly through Infrastructure as Code (IaC), eliminating human-driven actions and reducing deployment times from days to just minutes. Startups focused on continuous delivery greatly benefit from this speed, enabling them to conduct frequent production releases. The deployment readiness of environments remains consistent through IaC, as it prevents configuration errors. The pipeline system identifies coding errors before deployment, thus improving both reliability and trust in the deployment process. Teams gain more confidence due to IaC, leading them to deploy applications frequently and making IaC essential for maintaining operational efficiency.
Supporting Feature Branch Environments (Ephemeral Environments)
Teams working with workflows that use containerized applications and cloud resources depend on Infrastructure as Code (IaC) to create temporary environments for specific branch and feature testing. When developers open a pull request, it triggers IaC to set up a new testing environment that includes all necessary components for evaluation. The testing period ends with the dismantling of the environment to reduce costs. Each developer conducts tests independently through separate testing environments. This level of automation benefits startups, but remains optional for those who don’t require it. Effective IaC system designs should support modular constructs and parameters that allow deployment concurrency without conflicts.
Blue-Green and Canary Deployments
The implementation of blue-green deployment strategies through infrastructure automation allows developers to perform zero-downtime releases by switching traffic between two distinct sets of infrastructure, known as blue and green. Infrastructure as Code (IaC) enables the definition of these sets, facilitating the building of new stacks while the existing stack remains operational. Once testing is complete, IaC simplifies the easy destruction of the old stack. The deployment method known as canary releases introduces changes by adding new instances that receive partial traffic. IaC offers an efficient approach to creating and managing infrastructure, enabling safer deployment strategies that improve uptime during periods of increased customer demand.
Rollback and Recovery
Deployment failures can be managed more efficiently using Infrastructure as Code (IaC), which enables rapid recovery processes. Your previous infrastructure state, stored in code, allows you to revert to the last known stable configuration through a simple re-application process. You can deploy the last stable code version while running IaC for that version to ensure that the infrastructure aligns with the previous stable state when a new app version and its infrastructure fail. The process of quickly restoring previous states through IaC deployment is significantly faster than executing manual change reversals or system configurations based on memory recall. The IaC state provides clear visibility into the modifications that occurred in the infrastructure between different versions, assisting in identifying debugging targets.
Alignment with DevOps and Agile Practices
The DevOps methodology relies on Infrastructure as Code (IaC) because it enables development and operations teams to collaborate using tools like Git. PMs and POs can achieve faster release cycles, predictable deployments, and prompt user feedback, even though they do not directly engage with Infrastructure as Code. Through IaC, teams can quickly establish new environments, as the process requires minimal effort, allowing them to test their ideas more flexibly. IaC will enable PMs to create separate instances for clients in one day, while manual deployment takes weeks. Business agility improves through infrastructure adjustments, which can be performed as quickly as standard coding of new features.
Application lifecycle management receives IaC integration by implementing infrastructure procedures into deployment pipelines through tools such as Jenkins, GitHub Actions, and GitLab CI. Most teams deploy infrastructure updates before running application updates within a single release process. The GitOps model enables orchestration tools to perform automated infrastructure changes when repository updates occur. Startups will achieve safer and faster deployments through continuous user value delivery by treating infrastructure changes as a core part of the application’s lifecycle.
Current Industry Trends and the Future of IaC Adoption
The adoption of Infrastructure as Code has rapidly expanded over the last ten years, with organizations of various sizes increasingly implementing it. Startup owners and technology leaders should keep an eye on industry-level Infrastructure as Code trends, as this knowledge aids them in making strategic decisions and selecting appropriate tools. The future of IaC, along with its most important trends, includes:
Widespread Adoption and Multi-Cloud Management
The adoption of Infrastructure as Code (IaC) has evolved from a specialized use to an essential requirement for businesses, as 90% of DevOps teams now utilize it. Organizations require improved management of multi-cloud environments and complex cloud infrastructure, which IaC facilitates by providing enhanced visibility along with security and governance features. Startups adopt IaC due to its automated nature and clear configuration methods, and organizations are establishing standardization, thereby positioning IaC as a key operational competency for deployment and development teams. Knowledge of IaC will soon be mandatory for engineers, paralleling programming languages within the next few years.
GitOps: Infrastructure via Git and Continuous Delivery
The emerging GitOps concept has strong connections with Infrastructure as Code (IaC) since Git repositories serve as the definitive source of both application code and infrastructure information. Automated agents implement all changes that pass through the pull request process. IaC definitions in Git repositories are managed by continuous monitoring tools, including Argo CD, Flux, and Jenkins. This approach enables effortless rollbacks and audit tracking through Git’s version control capabilities. The GitOps method transforms infrastructure control into a software development process by integrating code examination and CI/CD pipelines along with drift detection systems. The maturation of tooling will drive GitOps adoption toward broader implementation by organizations that seek to enhance reliability and operational efficiency after adopting robust IaC practices.
Policy as Code and Automated Governance
The adoption of Infrastructure as Code (IaC) for automated infrastructure creation increases the need for Policy as Code (PaC), which enables automated governance and compliance. The practice of coding security rules allows for the evaluation of these policies before or after deployment. The enforcement of rules is achievable through three tools: Open Policy Agent (OPA), HashiCorp Sentinel, and Checkov. An implemented rule would prevent security groups from allowing open SSH access. The pipeline will fail if the developer attempts to include a policy in Terraform that violates established policies. This strategy allows organizations to reduce their risks, especially in fields requiring strict compliance standards, and startups can implement simple checks to avoid new problems by preventing open public S3 buckets.
Rise of Advanced IaC Tools and Abstractions
The infrastructure as code tool Terraform remains popular, yet higher-level abstractions for IaC are emerging as an industry trend. Through Pulumi, AWS CDK, and Azure’s Bicep, developers can combine application and infrastructure code using familiar programming constructs. AWS Proton joins other simple interfaces for infrastructure as code that cloud providers offer their customers. The open-source release of OpenTofu, which originated from Terraform, enables developers to engage in community-driven development. The ecosystem surrounding Terraform has expanded into new areas and shows promise for AI-assisted IaC tools that will simplify infrastructure management for non-professionals in the upcoming years.
AI and Automation in IaC
AI professionals are excited about its ability to enhance both DevOps systems and Infrastructure as Code (IaC) operations. The initial phase of tool development aims to utilize AI capabilities for optimizing cloud configurations by suggesting lower-cost instance types and detecting anomalous patterns in IaC. AI technology demonstrates the potential to translate product requirements, such as “highly available web service,” into code, which then generates IaC according to established best practices. The emerging AI-assisted IaC technology has the potential to simplify tasks and reduce errors, but users must maintain their infrastructure knowledge base. Startups should keep an eye on this space because AI may begin performing regular optimizations of Terraform merge requests while uncovering hidden issues.
Integration of IaC with Other “as Code” Concepts
The group examined Policy as Code and GitOps alongside Configuration as Code, Monitoring as Code, and Pipeline as Code, all of which combine into Everything as Code. This approach enables the management of Datadog and New Relic through APIs and code-based methods for configuring networks. The emerging field of platform engineering unifies various processes through teams that develop deployment templates for developers to use in infrastructure deployment, along with automatic setup for monitoring, logging, and CI pipelines. The DevOps toolchain transforms all software delivery procedures into coded systems, where Infrastructure as Code operates alongside other code-based components.
Growing Importance of Community and Standards
The adoption of IaC technology has led to standardization efforts and the development of interoperable standards, as demonstrated by the OpenTofu initiative, which maintains Terraform’s open-source nature. Startups benefit from using standard community modules and registry services that define default architectural patterns to avoid unnecessary development from scratch. Knowledge sharing about IaC within communities like Stack Overflow is increasing, resulting in better troubleshooting and learning opportunities. The quality of community modules will improve as cloud providers issue more guidelines regarding IaC structure and security.
Platform Engineering and Self-Service Infrastructure
The tech industry currently embraces Platform Engineering because it provides an intuitive platform for application deployment and infrastructure management to developers. The self-service tools in this approach simplify complex procedures by employing Infrastructure as Code (IaC) for provisioning. Developers can easily request services through the platform without needing to understand the IaC implementation, as those technical aspects are managed by platform team members. This enhances developer productivity and consistency, as startups and other organizations utilize tools such as Backstage for automated service fulfillment. The combination of Infrastructure as Code (IaC) with Platform as a Service (PaaS) will create future systems that enable users to leverage IaC flexibility while utilizing managed platform features.
Making Product Discovery Easier and More Accessible
Turn Your Vision into a Reality in Four Weeks with Our Expert-Driven TechBoost Program
See Product Discovery ServicesThe Future of Infrastructure: Why Embracing IaC Today Sets You Ahead
The essentiality of Infrastructure as Code (IaC) for system development continues to rise due to modern automation trends, policy as Code security measures, and user-friendly higher-level abstractions. Startups that remain aware of current trends increase their efficiency and reliability. Organizations that dismiss IaC create risks because infrastructure management becomes faster and more consistent when using this approach.
This guide explains the fundamentals of IaC, including its importance and benefits, as well as tool reviews- focusing on Terraform- and best practices, security guidelines, maintainability advice, application lifecycle integration, and industry forecasts for IaC. A non-technical executive should understand that IaC acts as an accelerator, enabling the safe and swift delivery of technology through its capacity to transform infrastructure into flexible, manageable assets that avoid becoming bottlenecks. Successful IaC implementation in your organization requires the technical details provided here to demonstrate both the rationale for implementation and specific methods for proper execution. The rapid industry shift towards IaC implementation gives businesses a competitive advantage in delivering value quickly and securely in cloud environments.
Key Takeaways
- IaC automates infrastructure management, improving efficiency and reducing errors.
- Benefits include faster deployments, consistency, cost optimization, and better collaboration.
- Security best practices involve proper secret management and implementing least privilege access.
- IaC integrates with application lifecycle management, enabling consistent environments and faster deployments.
- Future trends include widespread adoption, GitOps practices, and AI-assisted optimizations.