Homomorphic encryption might be the answer to Data breaches that have become an all-too-familiar headline in the ever-evolving digital age. And it’s not just about leaked passwords; it’s about safeguarding the myriad of personal information that could fall into unauthorized hands. Let me guide you if you’ve ever paused to wonder about the inner workings of secure data storage on servers. With over 12 years as a software engineer and architect, I’ve been at the helm of developing intricate encrypted systems. My journey has been enriched by architecting sophisticated software solutions for industry giants in FinTech, including notable projects like Tinka in the Netherlands and leading transport ventures such as CTC. Utilizing this extensive background, I aim to shed light on the intricate world of data encryption, specifically the growing significance of homomorphic encryption in our interconnected digital world.
Why Data Protection Matters?
In today’s digital ecosystem, data is a precious commodity, akin to gold or oil. Yet, with its rising importance comes the increased potential for misuse, making data protection paramount.
- Personal and Financial Security: The fundamental right to personal privacy extends to our online presence. Moreover, as our financial lives move online, unauthorized access could lead to identity theft, financial fraud, and emptied accounts. According to Security Intelligence, the average cost of data breaches rose by 2.6% to $4.35 million in 2022.
- Business Trust: A single data breach can significantly tarnish a brand’s reputation. Research from Oxford’s Journal of Cybersecurity highlighted that major breaches result in a 5–9% decline in a company’s reputational intangible capital.
- Regulatory Implications: Worldwide regulations like Europe’s GDPR and California’s CCPA emphasize strict data protection norms, with non-compliance leading to substantial penalties.
- Future-Proofing: With evolving technology, data generation will escalate. Investing in potent data protection tools today safeguards against tomorrow’s threats.
Drawing from my deep experience in the FinTech landscape, I’ve seen first-hand the critical role of data security. A standout solution in ensuring this security is homomorphic encryption, a concept we’ll explore further.
IT Consultancy for Strategic Advantage
Tailored IT Solutions to Drive Your Business Forward
Discover IT ConsultingIntroduction to Homomorphic Encryption
In the vast cybersecurity and data protection world, homomorphic encryption emerges as a revolutionary tool. But what exactly is it, and why has it garnered such attention, especially from professionals in the field like myself?
Defining Homomorphic Encryption
At its core, homomorphic encryption is a form of data encryption that allows computations to be performed directly on the encrypted data, without needing to decrypt it first. Think of it as working on a locked treasure chest – you can change what’s inside without needing to open it.
Imagine you have a sealed box with two apples inside. Without opening it, someone adds two more apples. Even though you never saw inside, you can confidently say there are four apples now. Homomorphic encryption operates similarly, allowing calculations without revealing the actual data.
Why It’s a Game-Changer?
Traditional encryption methods necessitate the decryption of data before any operation, making it vulnerable during the process. With homomorphic encryption, data remains encrypted throughout, mitigating risks of exposure. Let’s compare them:
- Traditional Encryption: Think of data as a book in a foreign language. You first need to translate (decrypt) it to understand or make changes. Once done, you retranslate (encrypt) and keep it safe. But during the translation, anyone can read the content.
- Homomorphic Encryption: Imagine the same book, but now you can make annotations and notes without ever translating it. The content remains safe, and you can still derive meaningful insights.
Real-world Applications for Homomorphic Encryption
Let’s consider cloud computing. Companies often store sensitive data on remote servers. With homomorphic encryption, they can execute operations on this data without ever decrypting it on the cloud, ensuring enhanced protection.
In healthcare, patient data stored in cloud servers can be analyzed for trends or anomalies without ever revealing individual patient information. Another example could be in finance: credit evaluations and risk assessments can be done using encrypted financial data, ensuring customer financial details remain confidential.
Experience the Power of Professional Web Development
Transformative Web Solutions Designed for Your Business Growth
Discover Web DevelopmentVariations and Types of Homomorphic Encryption
Homomorphic encryption isn’t a one-size-fits-all solution. It has variations like Fully Homomorphic Encryption, Somewhat Homomorphic Encryption, and Partially Homomorphic Encryption, each with its distinct features and applicable scenarios:
- Fully Homomorphic Encryption (FHE): Allows both addition and multiplication on encrypted data to be applied unlimited times. It’s like being able to perform any arithmetic operation on our sealed box of apples without ever looking inside;
- Somewhat Homomorphic Encryption (SHE): Permits a limited number of operations before the data needs decryption or becomes too “noisy” to use;
- Partially Homomorphic Encryption (PHE): Allows unlimited operations but only of a specific kind, such as addition OR multiplication, but not both.
Looking Ahead, as digital threats evolve, so must our defense strategies. Homomorphic encryption promises secure computations on encrypted data and is poised to be a cornerstone of next-gen data protection strategies.
Mathematics: The Backbone of Homomorphic Encryption
Software and mathematics have always been intertwined, each reinforcing the complexities and capabilities of the other. Within the realm of encryption, this relationship is particularly pronounced.
Mathematical Foundations in Software
All software, at its core, operates based on algorithms rooted in mathematical principles. The logical structures in coding, like conditions and loops, are direct representations of mathematical logic. For instance, even the fundamental IF… ELSE coding paradigm is an embodiment of conditional logic.
Visualization and Data Analysis
Beyond simple algorithms, the realms of graphics and data analysis also lean heavily on math. Graphics in applications and games utilize geometry, while machine learning models often involve concepts from linear algebra and statistics.
The Heart of Homomorphic Encryption
Encryption, especially techniques like RSA, relies profoundly on mathematical concepts, with prime numbers playing a pivotal role. Many encryption methods employ mathematical functions known for their computational asymmetry: they’re easy to execute in one direction, but not the other.
To illustrate, consider data encryption as a mathematical transformation. If y = x + 2 is our equation, and x is our data, adding 2 acts as a simple transformation. Real-world encryption utilizes more complex transformations for robust data protection.
In conclusion, understanding the deep connection between math and software is crucial when delving into sophisticated encryption methods, including homomorphic encryption.
Experience Our Research & Development Expertise
R&D-Led Software Development Integrates Innovation into Every Product Detail
Learn About R&D ServicesHomomorphic Encryption in Practice: A Simple Example
In the vast world of encryption, the concept of homomorphic encryption can be quite intricate. To make it more tangible, let’s explore a straightforward example.
The Problem: Protecting User Location Data
Imagine you own a food delivery app. Your application requires users to input their city for accurate service. While storing this data, you’d want to ensure maximum protection against potential breaches. However, you also need to run analytics, like determining the most popular delivery cities.
The Traditional Method
Traditionally, your server would store raw data like “San Francisco” or “New York.” These details can be exposed during a breach, posing privacy risks and potential legal implications.
Introducing Homomorphic Encryption
With homomorphic encryption, your server might store an encrypted version rather than the exact city name. For simplicity, let’s say “San Francisco” becomes “naS ocsicnarF” when encrypted.
Now, the beauty of homomorphic encryption is in its operational capabilities. Let’s say you want to know how many users are from San Francisco. Instead of decrypting the data first and then counting, the server can perform operations directly on the encrypted data. So, counting “naS ocsicnarF” occurrences will give you the number of San Francisco users without revealing their city.
Advantages of Homomorphic Encryption
This method ensures data privacy without compromising functionality. You’re able to garner insights from the data without exposing sensitive information. Moreover, operations on encrypted data reduce the risk of breaches during transmission or processing.
Limitations to Consider
However, certain operations, like finding restaurants near a user, might still require decrypted data. This is because you’d need accurate coordinates, which our simplified encryption example needs to provide. Thus, while homomorphic encryption offers substantial benefits, it’s essential to understand its scope and limitations in real-world applications.
In summary, homomorphic encryption revolutionizes the way businesses can handle and analyze data, balancing between user privacy and operational needs. This food delivery example is just a small peek into its vast potential applications in various industries.
Types of Homomorphic Encryption
Homomorphic encryption isn’t a one-size-fits-all solution. Different types of homomorphic encryption have been developed depending on the specific needs and nature of operations. Here’s a deeper dive into its main classifications:
1. Fully Homomorphic Encryption (FHE)
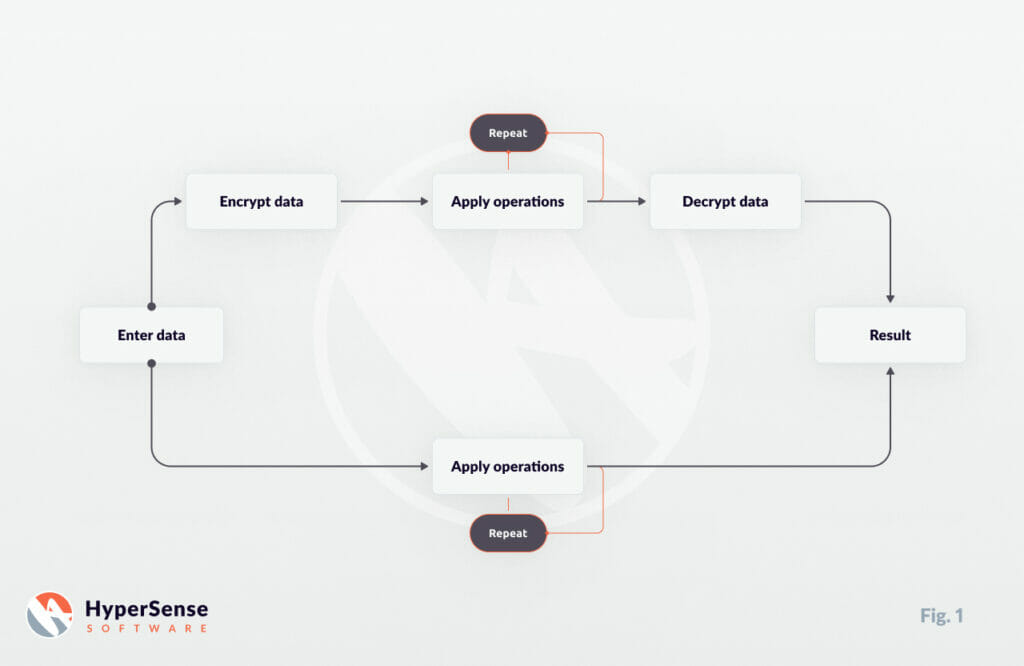
- Definition: In an ideal setting, Fully Homomorphic Encryption (FHE) permits an unlimited number of both addition and multiplication operations on encrypted data.
- Example: Imagine encrypted data representing numbers. With FHE, you can add or multiply these numbers together as many times as needed, and when decrypted, the result would match as if you had performed the same operations on the unencrypted data.
- Significance: The first concept of FHE was proposed way back in 1978. However, it wasn’t until 2009 that the first practical FHE scheme was constructed, marking a monumental leap in the field of cryptography.
2. Somewhat Homomorphic Encryption (SHE)

- Definition: Somewhat Homomorphic Encryption (SHE) allows operations on encrypted data, but there’s a cap on how often these operations can be executed.
- Example: Consider encrypted images in a database. SHE might let you apply a certain filter to these images, but only for a limited number of times before the encryption starts to degrade or become less reliable.
- Significance: While the limitation may sound restrictive, there’s often a known upper limit to the number of operations needed in real-world applications. SHE can be tailored to fit these specific requirements, making it a feasible option for many use cases.
3. Partially Homomorphic Encryption (PHE)
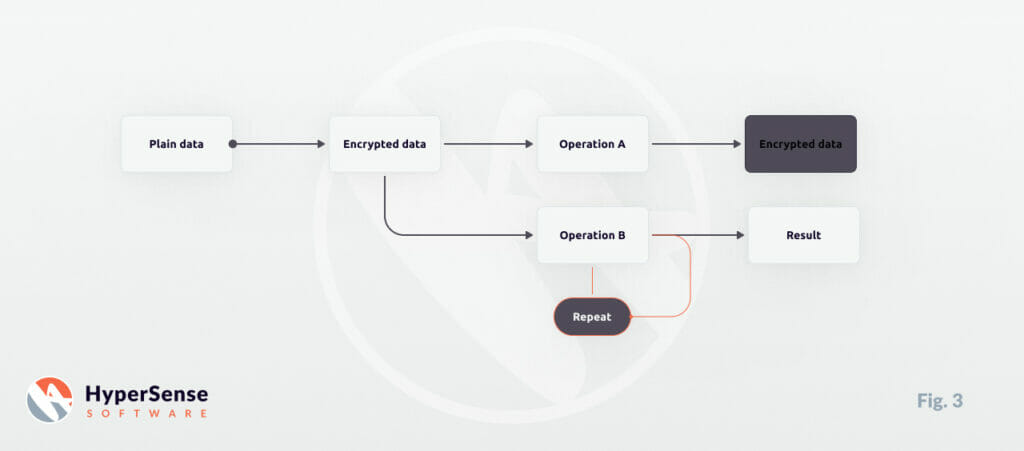
- Definition: PHE focuses on specifics. While there’s no restriction on the number of times operations can be done, only certain types of operations can be performed on the encrypted data.
- Example: Imagine encrypted text messages. A PHE system might allow you to search for specific keywords within the encrypted messages (a specific operation) without ever decrypting them, but you couldn’t perform other operations like text translation.
- Significance: Many familiar encryption schemes, including RSA, fall into this category. The targeted nature of PHE means that it can be optimized for specific tasks, providing efficient performance for those operations.
Understanding the distinctions between these types of homomorphic encryption is crucial when deciding the best fit for a particular application or system. Each offers a unique blend of flexibility, security, and functionality, ensuring data privacy while still enabling meaningful data operations.
Selecting the Right Homomorphic Encryption Approach
Navigating the realm of homomorphic encryption can be daunting, especially with its multiple types and intricacies. The selection process isn’t merely about understanding the technical specifications, but more about aligning them with a project’s specific needs and demands. Here’s a guideline to help you make an informed decision:
1. Assess Your Needs
Before diving into which type of homomorphic encryption to use, understand the nature of your data and operations:
- Volume of Data: Larger datasets might require more processing power, especially when running computations on encrypted data.
- Type of Operations: Are you looking for simple tasks like search or more complex analytics? This can determine whether you need PHE, SHE, or FHE.
- Frequency of Operations: If your system frequently runs operations on encrypted data, it could guide your choice between SHE and FHE.
2. Consider the Trade-offs
Every encryption approach comes with its set of pros and cons:
- Performance vs. Flexibility: While FHE provides immense flexibility, it might not be as performance-efficient as SHE or PHE for certain tasks.
- Complexity vs. Security: Sometimes, the most secure solutions can be complex to implement. Weigh the benefits of heightened security against the potential challenges in implementation.
3. Scalability Concerns
Think long-term. Your chosen approach should not only cater to your immediate needs but also be scalable:
- Growth in Data: As your data grows, will the chosen encryption method still perform efficiently?
- Emerging Needs: Industries evolve, and so do their data processing needs. Ensure that your chosen encryption type can adapt to new or more complex operations in the future.
4. Infrastructure and Resources
The choice of homomorphic encryption might also be influenced by the infrastructure you have in place:
- Computational Resources: FHE, for instance, is computationally intensive. Do you have the required resources to support it?
- Expertise: Do you have access to personnel skilled in implementing and managing the chosen encryption type?
Redefine Your Project with Our Development Teams
Fuel Your Projects with Tailored Software Development Expertise
Get Your Development Team5. Regulatory and Compliance Concerns When Using Homomorphic Encryption
Finally, always keep the regulatory landscape in mind:
- Data Protection Laws: Depending on the jurisdiction, there might be specific guidelines on how user data should be encrypted and processed.
- Industry Standards: Especially crucial for sectors like FinTech or HealthTech, where data privacy and protection are paramount.
The journey to selecting the right homomorphic encryption isn’t about picking the most advanced or recent method but choosing the one that aligns best with your needs, resources, and future aspirations. It’s a strategic decision that can shape the security and efficiency of your data-driven initiatives.
Embracing the Future of Secure Data Processing
In our digital era, data has become a new form of currency. As businesses, institutions, and individuals generate and process vast amounts of information daily, the demand for advanced security mechanisms has never been higher. Homomorphic encryption stands out as a beacon in this context, ushering us into a realm where we can compute encrypted data without compromising its confidentiality. Its potential in reshaping industries, from finance to healthcare, by offering an unprecedented blend of privacy and utility, is immense.
However, as with any technology, its implementation requires careful planning and a nuanced understanding. The various types of homomorphic encryption cater to different needs and have their distinct benefits and challenges. As we’ve explored in this article, the journey to choosing the right approach is rooted in introspection – understanding your specific needs, the nature of your data, the operations you require, and the resources at your disposal.
Yet, homomorphic encryption’s promise is clear: a world where our data remains our own, even as we unlock its potential through analytics, AI, and more. It’s not just about security; it’s about enabling innovation without barriers, where data-driven insights are harvested without sacrificing privacy.
Ready to Secure Your Data’s Future?
Are you contemplating the leap into homomorphic encryption? Whether you’re just starting your journey or seeking to refine your existing systems, our team of experts is here to guide and support you. With the profound transformations reshaping our digital landscape, ensure you have the best tools and knowledge to navigate them confidently.
Contact us today, and let’s embark on a journey to redefine your data security strategy.
Frequently Asked Questions on Homomorphic Encryption
What is the difference between encryption and homomorphic encryption?
When using traditional encryption methods, you first need to decrypt data before making changes or gaining insights. When you use homomorphic encryption, the data remains encrypted even as it is sent, processed, or changed. This reduces the risks of data exposure to bad actors or those using it for nefarious purposes.
Can homomorphic encryption be practical?
It’s feasible to use homomorphic encryption, but you do need to consider some factors in relation to your product. Elements such as data volume, scalability, and the overall complexity of the data can help you decide if homomorphic encryption is the best option for your software.
Is fully homomorphic encryption possible?
At some point, but not right now. The hardware required to process the encrypted data is still in its early stages, and the investment required to get FHE possible might not be feasible for some companies. In addition, some data that your software might utilize is already decrypted by default so you will need to encrypt it first to have a true, fully homomorphic encryption environment.